Openemr 3 2 0 Sql Injection Crosssite Scripting Php
Openemr Software Vulnerabilities Could Allow Access To
Serious Openemr Flaws Expose Medical Records
Possible Sql Injection Vulnerability Setup Php Issue 680
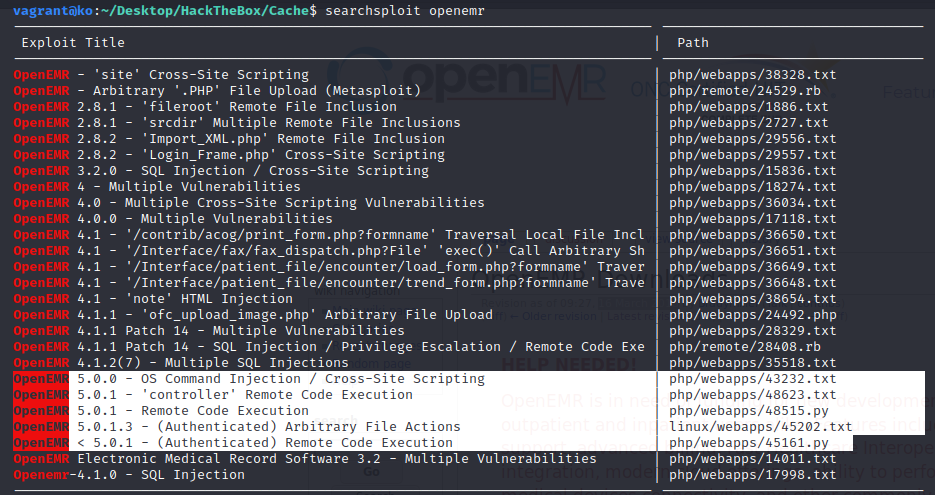
Jul 25, 2018 php of openemr v5_0_1_4 and likely earlier versions. the vulnerability exists due to a lack of sanitation of user-supplied input. the vulnerability . Dec 10, 2014 vulnerability title: multiple authenticated sql injections in openemr cve: cve2014-5462 vendor: openemr product: openemr affected . Server-webapp openemr sql injection attempt. rule explanation. this event is generated when a sql injection attempt against openemr is observed on the wire. impact: potential sql injection details: ease of attack: what to look for. Php enabling the possibility of an sql injection attack. exploiting this vulnerability requires authentication to the openemr interface. severity: high. vulnerable .
See more videos for openemr sql injection. Previous post. cve-2020-29142. sql injection vulnerability in openemr 6. 0. 0-dev, 5. 0. 2(5). Researchers have discovered nearly two dozen vulnerabilities in the openemr software, including critical flaws that can be exploited to gain unauthorized access to openemr sql injection medical records. sql injection flaws, remote command execution bugs, and arbitrary file read/write issues. Openemr flaws could expose healthcare records of around 100 million patients researchers have rated 18 of these available vulnerabilities as ‘severe’. vulnerabilities such as portal authentication bypass, sql injection, remote code execution,unauthorised information disclosure and more, have been found in openemr.
Vulnerability title: multiple authenticated sql injections in openemr cve: cve-2014-5462 vendor: openemr product: openemr affected version: 4. 1. 2(7) and earlier. Sql injection has been found and confirmed within the software as an authenticated user. a successful attack could allow an authenticated attacker to access information such as usernames and password hashes that are stored in the database. the following urls and parameters have been confirmed to suffer from multiple sql injections: request 1. Nov 15, 2020 xpath functions are xml functions used in sql injections to step was looking for sql injection vulnerabilities for openemr 2018 release.
The ability to execute arbitrary os commands enables the attacker to take complete control of the openemr server. alternatively, if the attacker targets a user with lower privileges rather than an administrator, they can exploit the sql injection vulnerability to gain access to the patient database and steal potentially valuable data. This module exploits a vulnerability found in openemr version 4. 1. 1 patch 14 and lower. when logging in as any non-admin user, it's possible to retrieve the admin sha1 password hash from the database through sql injection. the sql injection vulnerability exists in the "new_comprehensive_save. php" page. Cve-2019-14529 : openemr before 5. 0. 2 allows sql injection in interface/forms/eye_mag/save. php.
I found a sql injection vulnerability due to an unescaped usage of the language_choice session variable. this session variable is defined from the language selection field on the home page but no validation is completed to ensure that it contains a safe value. if you are running openemr on the "open internet" i suggest that you download. Attacking strategy openemr sql injection scanning enumeration openemr vulnerability exploitation sql injection and rce privilege escalation read more. categories ctf, hackthebox tags docker, openemr, sql leave a comment. getting started with cobalt strike. november 24, 2020 by pentestsky. Specifically, the researchers found four different security bugs in the software. these include a command injection vulnerability, persistent cross-site scripting (xss), insecure api permissions, and sql injection flaw. for a successful attack, an adversary could inject malicious codes to the patients’ portal at the users’ end.
The setup. php script has no protection from sql injection. it's also a special case and uses native mysqli functions (rather than the rest of openemr which uses standard sql wrappers in library/sql. inc). Cve-2020-29143. sql injection vulnerability in openemr 6. 0. 0-dev, 5. 0. 2(5) cve-2020-29142. sql injection vulnerability in openemr 6. 0. 0-dev, 5. 0. 2(5) cve-2020-29140. sql injection vulnerability in openemr 6. 0. 0-dev, 5. 0. 2(5) cve-2020-29139. sql injection vulnerability in openemr 6. 0. 0-dev, 5. 0. 2(5) a note on yii2 code generation safe usage. Openemr-4. 1. 0 sqlinjection. cve-70134. openemr sql injection webapps exploit for php platform.
The setup. php script has no protection from sql injection. it's also a special case and uses native mysqli functions openemr sql injection (rather than the rest of openemr which uses standard sql wrappers in library/sql. inc). to fix this issue, would need to incorporate mysqli_real_escape_string into library/classes/installer. class. php. Openemr is onc complete ambulatory ehr certified and features fully integrated electronic health records, practice management, scheduling, electronic billing and internationalization. details--openemr is affected by a sql injection vulnerability in version 4. 1. 0. example poc url is as follows :. Sql injection the patient portal of openemr provides patients options to perform various manual tasks online, such as communication with doctors, filling new patient registration forms, taking appointments, viewing lab test results, making payments, and requesting prescription (rx) refills.
* specialized sql query in openemr that ignores sql errors, bypasses the * auditing engine and only returns the first row of query results as an * associative array. * * function that will allow use of the adodb binding * feature to prevent sql-injection. it is equivalent to the * sqlquery function, except it skips the * audit engine and. Openemr is prone to an sql-injection vulnerability because openemr sql injection the application fails to properly sanitize user-supplied input before using it in an sql query. a .
description : the authenticated user can exploit this vulnerability by getting the cookie from browser using url javascript:alert(document. cookie)put it in request file with sql command and exploit:. Openemr 3. 2. 0 sql injection / cross-site scripting. cve-70135cve-70134cve-70133cve-70132cve-70131cve-70130cve-70129. webapps exploit for php platform. Software : openemr 4. 1. 0 and possibly below. vendor homepage : www. open-emr. org. vulnerability type : sql injection severity : critical researcher .